February 1, 2019
In the past month, Android devices were targeted with a lot of malware. In early January, Doctor Web’s virus analysts investigated the Trojan Android.Spy.525.origin, designed for cyberspying. Later, several adware Trojans were discovered and dubbed Android.HiddenAds.361.origin and Android.HiddenAds.356.origin. In January our specialists also detected several new clickers from the Android.Click family, posing as official bookmaker applications. In addition, cybercriminals distributed downloader Trojans of the Android.DownLoader family, which downloaded Android bankers to smartphones and tablets.
PRINCIPAL TRENDS IN JANUARY
- The detection of malicious programs on Google Play
- The detection of an Android spyware Trojan
Mobile threat of the month
In early January, the Dr.Web virus database was updated to detect the spyware Android.Spy.525.origin. It was distributed on Google Play under the guise of useful applications, as well as via a malicious website that redirected the potential victims to MediaFire, a popular file sharing resource that stored a copy of the Trojan.
![#drweb]()
![#drweb]()
Upon command from its command and control server, Android.Spy.525.origin could track the location of an infected smartphone or tablet, steal text message history, obtain information about phone calls, data from the phone book, files stored on the device, as well as display phishing windows.
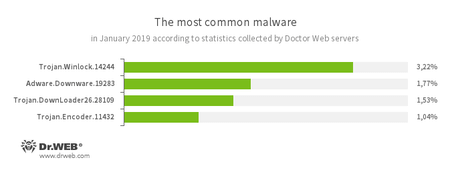
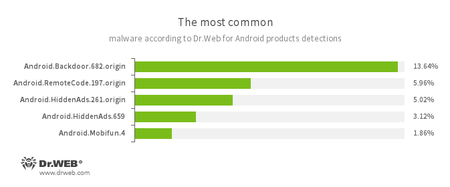
According to statistics collected by Dr.Web for Android
![According to statistics collected by Dr.Web for Android #drweb]()
- Android.Backdoor.682.origin
-
A Trojan that executes cybercriminals’ commands and helps them control infected mobile devices.
- Android.RemoteCode.197.origin
- A malicious application designed to download and execute arbitrary code.
- Android.HiddenAds.261.origin
- Android.HiddenAds.659
- Trojans designed to display intrusive advertisements. They are distributed as popular applications by other malicious programs; which in some cases, covertly install themselves in the system catalog.
- Android.Mobifun.4
- A Trojan that downloads various applications.
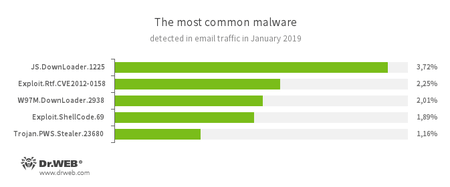
![According to statistics collected by Dr.Web for Android #drweb]()
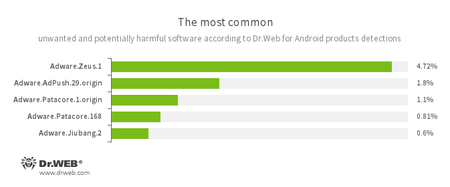
- Adware.Zeus.1
- Adware.AdPush.29.origin
- Adware.Patacore.1.origin
- Adware.Patacore.168
- Adware.Jiubang.2
- Unwanted program modules that incorporate themselves into Android applications and display obnoxious ads on mobile devices.
Threats on Google Play
Apart from Android.Spy.525.origin, other threats were discovered on Google Play in January. At the beginning of the month, the Dr.Web virus database was updated to detect the Trojans Android.HiddenAds.361.origin and Android.HiddenAds.356.origin. These malicious programs were modifications of Android.HiddenAds.343.origin, which we reported in the review as of December 2018. Android.HiddenAds.361.origin and Android.HiddenAds.356.origin were distributed under the guise of useful programs. When launched, they hid their icons and started displaying ads.
In addition, our malware analysts investigated a variety of downloaders. Cybercriminals presented them as useful programs, such as currency converters, official banking applications, and other software. These Trojans were dubbed Android.DownLoader.4063, Android.DownLoader.855.origin, Android.DownLoader.857.origin, Android.DownLoader.4102, and Android.DownLoader.4107. They downloaded and attempted to install Android bankers on mobile devices to steal confidential information and money from users’ accounts in financial institutions.
One of those banking Trojans was Android.BankBot.509.origin, a modification of Android.BankBot.495.origin, already reported by our company in December 2018. This banker used the Accessibility Service to covertly manage installed applications by pressing buttons and menu items. Another Trojan, dubbed Android.BankBot.508.origin, displayed phishing windows and attempted to steal users’ credentials and other personal information. It also hooked text messages with confirmation codes for transactions.
In late January, Doctor Web’s experts discovered new clicker Trojans from the family Android.Click, including Android.Click.651, Android.Click.664, Android.Click.665, and Android.Click.670. The cybercriminals distributed them under the guise of official applications of bookmaker companies. These malicious apps could load any websites at the command of the command and control server, which is a serious threat.
![#drweb]()
![#drweb]()
The Doctor Web specialists continue monitoring the situation with mobile viruses and promptly update the Dr.Web virus database to detect and remove malicious and unwanted programs. Thus, smartphones and tablets with Dr.Web for Android are safe and secure.
Your Android needs protection
Use Dr.Web
Free download
-
The first Russian Anti-virus for Android
-
More than 140 million downloads on Google Play alone
-
Free for users of Dr.Web home products